Network Security
Given the nature of our work involving data ingestion and warehouses, ensuring network security has been of utmost importance to us. We have implemented comprehensive security measures to establish a highly secure infrastructure and application environment.
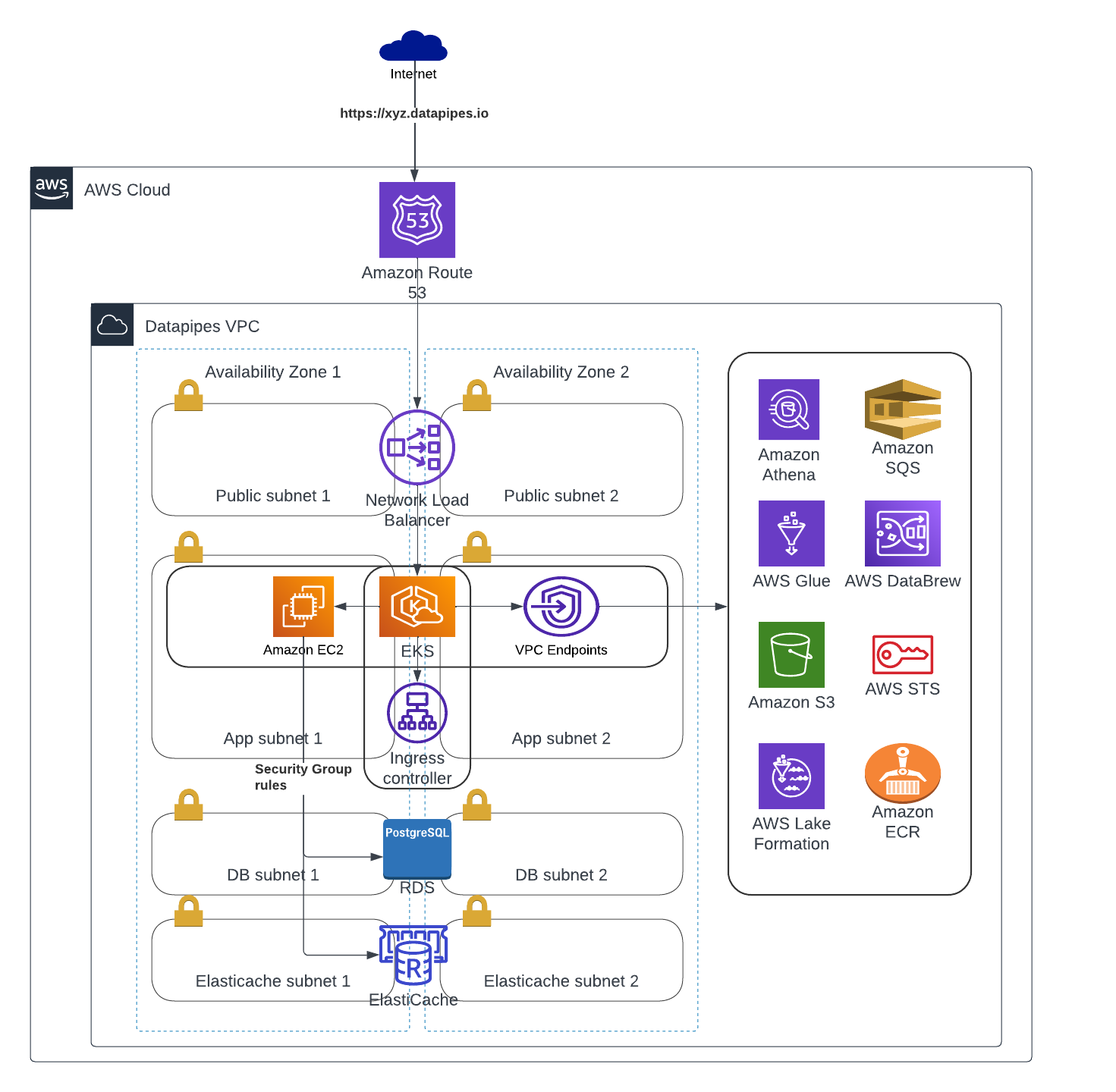
Datapipes Standard architecture
We have a standard setup that we offer as a part of our infrastructure deployment
SSL
SSL plays a critical role in securing communications over the internet, ensuring the confidentiality, integrity, and authenticity of transmitted data. To ensure secure communication, we have implemented SSL on the public AWS load balancer. The SSL certificate is managed through the LetsEncrypt Cert manager, although we also have the option to use other certificate managers like AWS Certificate Manager. By offloading SSL within the EKS cluster, all web traffic to the application remains encrypted throughout.
Dedicated VPC Subnets
For optimal network organization, we establish dedicated VPC subnets for various components such as the EKS cluster, RDS DB instance, and Elasticache instance. Private subnets are specifically designated for hosting the EKS cluster and its nodes. Furthermore, separate private subnets are created for the Database and Elasticache instances, ensuring that they are not directly accessible from the Internet.
Restrictive Security Group(Firewall) rules
To enforce strict access controls, we employ security groups. These security groups are configured to permit traffic to the Database instance and Elasticache instance exclusively from within the application. Similarly, traffic to the application is allowed only from the load balancer endpoint. This ensures that only authorized sources can interact with the respective components while maintaining a robust firewall.
VPC Endpoints
To enhance security and efficiency, we utilize VPC endpoints to establish direct communication with various AWS services, including Athena, Glue, Macie, Databrew, S3, EC2, and ECR. By employing VPC endpoints, we ensure that the traffic originating from our application does not traverse the public network. Instead, it remains confined within the secure confines of the AWS network. This approach guarantees that all data exchanged between the application and these services remains protected and isolated from external networks.
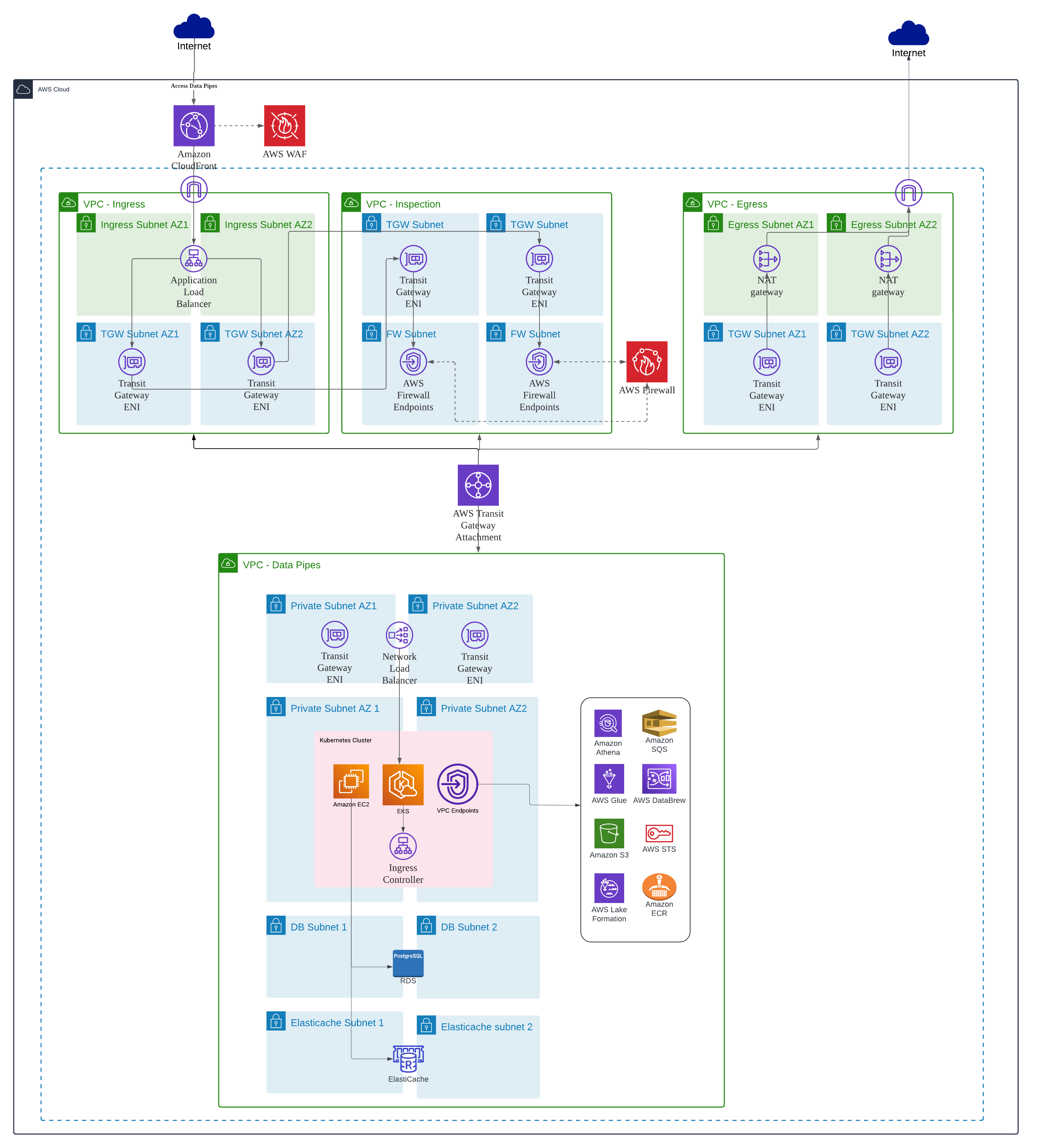
Let’s make it more secure
In addition to our standard deployment, we also offer a more secure infrastructure deployment of Datapipes. It has a few more components in addition to the above-mentioned.
CloudFront
To further enhance network security, we leverage CloudFront and AWS ALB (Application Load Balancer). CloudFront provides robust security features, including built-in DDoS protection at both the network and application layers, as well as SSL/TLS encryption. Additionally, CloudFront offers flexible access control mechanisms such as geographical restrictions and IP whitelisting/blacklisting, enabling granular control over web application access based on source IP addresses. By acting as a protective layer between the origin server and the internet, CloudFront mitigates the load on the origin server and strengthens its security by minimizing direct exposure to the public internet.
Web Application Firewall
To improve network security, we augment our measures with the implementation of AWS WAF (Web Application Firewall). This powerful tool offers a host of network security advantages, including shielding our applications against prevalent web-based attacks like SQL injection, XSS, and CSRF. AWS WAF offers a comprehensive set of pre-configured rules designed to combat common threats, while also granting us the flexibility to craft custom rules tailored to our specific application's security needs. This level of customization empowers us to establish granular security policies and fine-tune rule sets according to our client’s unique security requirements.
Multi VPC architecture
This architecture employs a multi-VPC approach, with each VPC serving a specific function. One VPC handles ingress traffic, another manages egress traffic, a separate VPC is dedicated to AWS Network Firewall for network traffic inspection, and finally, there's the VPC designated for deploying datapipes. These VPCs are interconnected through a Transit Gateway. By adopting this configuration, direct internet traffic to the Datapipes VPC, where the application resides, is strictly prohibited, ensuring a high level of security.
Network Firewall
We leverage AWS Network Firewall, a tool that allows us to create precise firewall rules for granular control over network traffic. Network Firewall works together with AWS Firewall Manager so we can build policies based on Network Firewall rules and then centrally apply those policies across all the VPCs in a centralized manner. This streamlined approach ensures consistent and robust network security throughout our infrastructure.
